Fiber Network Security: Protect Your Fiber Optic Infrastructure from Cyber Threats
Fiber Network Security: Protect Your Fiber Optic Infrastructure from Cyber Threats
Blog Article
Comprehending the Value of Information and Network Protection in Today's Digital Age
In an age where digital makeover is important to business success, the significance of information and network safety and security has actually never ever been a lot more obvious. As companies significantly incorporate innovative technologies, they also reveal themselves to a myriad of cyber risks that can compromise sensitive information and interfere with operations. Recognizing the effects of data violations, along with the crucial safety and security measures required to reduce these risks, ends up being vital. However, the challenge lies not only in executing these procedures but additionally in growing a proactive protection society within organizations. This discussion will certainly discover these complexities further and disclose vital understandings on guarding electronic properties.
The Surge of Cyber Dangers
The landscape of electronic security has become progressively perilous as cyber threats multiply around the world. Organizations throughout various fields are encountering a rise in advanced attacks, varying from ransomware to phishing plans. These hazards not just endanger sensitive data yet additionally interrupt organization procedures, bring about significant financial losses and reputational damage.

Furthermore, the development of innovative strategies such as synthetic intelligence and maker understanding has geared up assailants with the tools to automate their procedures, making it significantly testing for traditional protection actions to keep up. As businesses navigate this treacherous landscape, the urgency for durable information and network protection approaches has actually never ever been better, highlighting the need for attentive surveillance, timely updates, and worker awareness to mitigate these escalating threats.
Effects of Data Violations
Information violations can have extreme and significant effects for companies, affecting not only their economic standing however additionally their reliability and client trust fund. When delicate info is compromised, companies often face straight monetary losses as a result of lawful costs, regulative fines, and the prices connected with event response. In addition, the long-lasting effects can be a lot more harmful; a ruined online reputation may result in shed business possibilities and decreasing customer retention.
The disintegration of client trust is probably the most dangerous repercussion of an information breach. Customers may wonder about a company's capacity to shield their individual info and, consequently, may select to take their organization somewhere else. This loss of self-confidence can bring about lowered profits and market share.
Additionally, organizations might experience increased examination from stakeholders and regulatory authorities, leading to a more challenging functional atmosphere. The emotional influence on employees, that might feel much less secure or valued, can likewise influence productivity and morale.
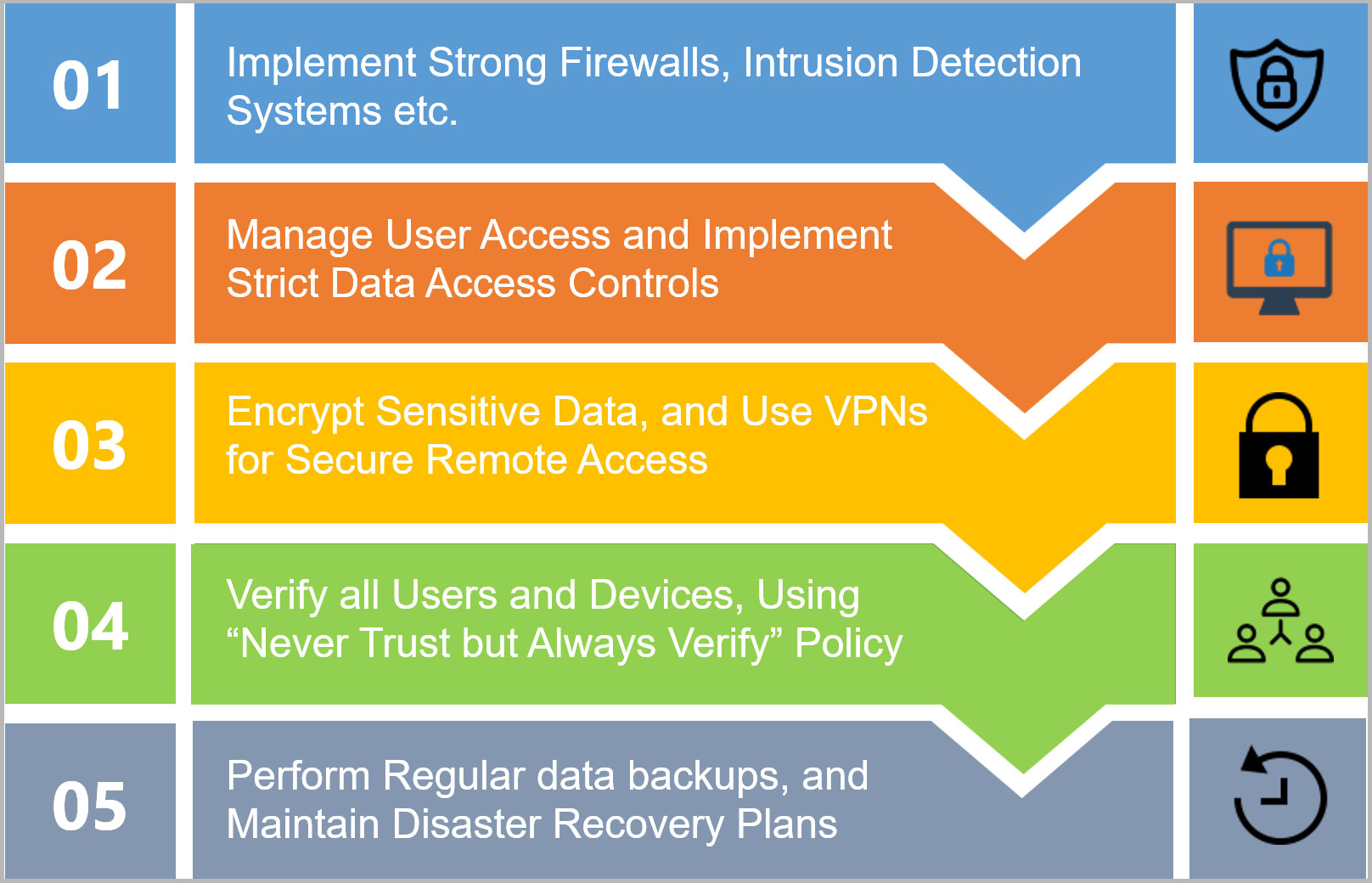
Vital Safety And Security Measures
Implementing important safety and security steps is essential for protecting sensitive information and preserving organizational stability. Organizations needs to embrace a multi-layered safety approach that encompasses both physical and electronic safeguards.
One of the foundational actions is to develop durable gain access to controls, guaranteeing that only licensed workers can access sensitive data. This can be attained through solid password plans, multi-factor verification, and regular audits of individual access legal rights. In addition, encrypting information both en route and at remainder gives a crucial layer of defense against unapproved accessibility.
Regular software application updates and spot monitoring are also essential, as they aid alleviate vulnerabilities that could be exploited by malicious stars. Organizations should execute firewalls and breach detection systems to monitor network web traffic and recognize prospective hazards proactively.
Moreover, performing normal protection assessments and penetration testing makes it possible for companies to determine weak points in their defenses prior to they can be manipulated. Employee training on safety and security recognition is equally important, as human error remains one of the leading sources of data breaches. By incorporating these essential safety procedures, organizations can substantially decrease their threat exposure and boost their durability against cyber threats.
Building a Safety And Security Society
Creating a reliable security culture within an organization is an important complement to executing robust safety measures. A safety and security culture promotes an atmosphere where workers comprehend the significance of safeguarding sensitive info and are actively engaged in safeguarding it. This society is grown through thorough training programs that stress the relevance of data safety and security and the prospective threats connected with carelessness.
Leadership plays a vital role in developing this culture. Workers are much more most likely to embrace comparable mindsets when execs prioritize protection and demonstrate their dedication. Regular communication regarding security updates, policies, and treatments guarantees that every person stays vigilant and educated
Motivating open discussion regarding security problems equips workers to report dubious activities without concern of retaliation. Applying a rewards system for positive behavior can even more incentivize individuals to browse this site take possession of safety methods.
Furthermore, carrying out simulations and drills assists enhance the importance of preparedness check my blog and action. By integrating security into decision-making processes and daily operations, companies can produce a resistant labor force with the ability of adjusting to evolving dangers. Inevitably, a solid protection society not only safeguards information yet also improves general organizational integrity and credibility.
Future Trends in Data Safety And Security
Advancing and emerging innovations cyber risks are reshaping the landscape of data safety and security, triggering organizations to adjust their techniques appropriately. One considerable pattern is the enhanced adoption of expert system (AI) and equipment understanding (ML) for hazard discovery and action. These innovations allow more aggressive protection procedures by examining vast amounts of data to identify abnormalities and prospective breaches in real-time.
One more fad is the step towards zero-trust protection versions, which run under the concept that no user or gadget need to be trusted by default. This strategy highlights continuous verification and minimizes accessibility to delicate data based upon strict authentication processes.
Furthermore, the surge of remote work has actually sped up the need for durable endpoint safety and security solutions that secure devices outside typical network perimeters - data and network security. As companies welcome cloud computing, protecting data in transportation and at rest has actually become extremely important, causing the development of sophisticated security methods
Verdict
In conclusion, the importance of data and network safety and security can not be overemphasized in the modern electronic landscape. As cyber dangers proceed to rise, organizations should continue to be aggressive and cautious in applying thorough security measures.
In a period where electronic improvement is essential to company success, the importance of data and network security has never ever been more noticable. Understanding the effects of information breaches, alongside the crucial protection measures required to minimize these threats, comes to be vital.Producing an effective security society within an organization is an important enhance to carrying out robust protection procedures.Emerging modern technologies and progressing cyber dangers are reshaping the landscape of information safety, prompting organizations to adjust their strategies as necessary.In conclusion, the significance of information and network protection Go Here can not be overstated in the contemporary electronic landscape.
Report this page